
Long Reads
Hitman-for-hire darknet sites are all scams. But some people turn up dead nonetheless
I did not know Bryan Njoroge. I had never met him, talked to him, or
encountered him online. In ordinary circumstances, I would have never
heard of his death, more than 6,500 kilometres away. Yet in late June
2018, a message arrived in my inbox. Its subject read: “Suicide (or
Murder)?” The email contained a link to a webpage showing unequivocally
that someone wanted Bryan dead.
On May 29, a person
calling themselves Toonbib had exchanged messages with someone they
thought was a Mafia capo renting hitmen on the dark web.
Toonbib had sent a picture of Njoroge in a suit, lifted from a school
yearbook, and an address in Indiana where Njoroge – a soldier, who
usually resided at a military base in Kentucky – would stay for a few
days. “He will only be in location from june 01 2018- june 11,” Toonbib
wrote. They paid about $5,500 in bitcoin for the hit.
The
day after, Toonbib started chasing the presumed capo for an answer,
which took some more time to arrive. “I will assign an operative to your
job and it will be done in about a week, is this ok? I will get back to
you shortly with an estimated date,” the capo wrote on June 1. Toonbib
never answered. On June 9, Bryan Njoroge was found with a fatal gunshot
wound to the head, near a baseball field in Clarksville, Indiana. His
death was recorded as a suicide.
There are no hitmen in this story. There are no
sharply dressed assassins screwing silencers on to their Glocks, no
operatives assigned, nor capos directing them.
There
is a website, though – a succession of websites, to be precise – where
all those things are made out to be true. Some people fall for it.
Looking for a hitman, they download Tor, a browser that uses encryption
and a complex relaying system to ensure anonymity, and allows them to
access the dark web, where the website exists. Under false names, the
website’s users complete a form to request a murder. They throw hundreds
of bitcoins into the website’s digital purse.
The website’s admin is scamming them: no
assassination is ever executed. The admin would dole out a hail of lies
for why hits had been delayed, and keep the bitcoins.
But,
elsewhere, someone called Chris Monteiro has been disrupting the
website’s operations for years, triggering its admin’s wrath.
In 2016, two years before sending me the email
about Njoroge, Monteiro was just a guy writing wikis. A tall man in his
thirties with thick sable hair, a short beard and deep-set, dark eyes,
Monteiro is a man of weird pastimes. By day, he worked as a computer
system administrator for a London-based firm; by night, he turned on a
six-screen desktop computer in his South London flat and spent hours
plumbing the depth of the internet. He called himself a “cybercrime and
niche topic internet researcher”. He was into transhumanism, the
internet-based movement advocating for human enhancement and
immortality. He gave talks about the politics of sci-fi, using a
slightly slurred patter. He knew a great deal about credit card fraud.
But his passion was the dark web.
This was the
perfect environment for scammers – impenetrable to search engines and
rife with illegality. Online forums crawled with references to sentient
AIs lurking in the dark web, live-streaming websites showing people
being slaughtered in “red rooms”, or dark web pages revealing the secret
of the Illuminati. “This weird fringe of the internet, it's one of the
toughest areas to seek truth,” Monteiro says.
In
2015, Monteiro started running the r/deepweb subreddit, a front row on
the day-to-day happenings of the online netherworld. He documented his
findings on his blog – pirate.london – and on online encyclopedias, such
as Wikipedia and anti-pseudoscience website RationalWiki. He made it
his mission to kill urban legends – he contributed to Wikipedia’s
articles on the dark web and darknet market, and created RationalWiki’s
pages about red rooms and runaway AIs.
He also wrote RationalWiki’s article about internet assassination. The rumour that you could hire a contract
killer on the dark web in exchange for bitcoin had been around since
the early 2010s. That was because, unlike snuff movies and evil AIs,
hitman-for-hire services were ubiquitous on the dark web. Some were
structured as “prediction markets”, with users crowdfunding the
assassination of VIPs and politicians; or they could be catering to the
private grudge-bearer wanting to book a hit via private chat.
Monteiro’s
research suggested all such websites to be either harmless trolling or
scams designed to rob people of their bitcoins. He could find no
evidence of anybody ever being killed by a hitman hired online, nor of
any hitman working online. He wrote this all on RationalWiki. With
footnotes.
Then, on February 20, 2016, an anonymous
user made an edit to the internet assassination article. The edit,
Monteiro says, added something to the effect of “all assassination sites
are scams, except for Besa Mafia, which is real”, appending a link to a
dark web site. (The edit was permanently deleted by RationalWiki’s
admins at Monteiro’s urging; but a subsequent modification by the same user remains in the edit history. “An other site is Besa
Mafia, a marketplace where hitmen can sign up to provide their services
and where customer can order, [sic]” the edit read. “The site protects
the customers with an escrow service that stores the bitcoin until the
job is completed. They also accept external escrows.”)
Monteiro
understood this to be shameless self-promotion. The people running Besa
Mafia, whatever that was, had seemingly vandalised his finely crafted
piece of wiki-scholarship in order to shill for their assassination
website. “I went, ‘What the fuck is this shit?,’” he says. “This is not
only nonsense, it's someone promoting a scam on my article.”
He
fired up Tor and went to the Besa Mafia website. Ostensibly run by
Albanian gangsters (“besa” is Albanian for “honour”), it was littered
with poor English, stock pictures of armed beefcakes, and a payment
system that – far from protecting customers’ bitcoin – allowed whoever
ran the website to easily snatch the funds. He wrote a scathing review of Besa Mafia on his blog, calling it a scam.
A few days later, someone from Besa Mafia got in
touch. “Helo, I am one of the admins of the Besa Mafia website on deep
web [sic],” the email read. “Would it be possible for us to pay for a
true and honest positive review? Let me know if we can prove to you that
we are legit.” It was signed “Yura”.
A
back-and-forth exchange ensued. Monteiro gleefully bombarded Yura with
questions, punching holes in the site’s business model, security and
technical makeup. For Monteiro, it was obviously a scam. But, while Yura
acknowledged the website’s shortcomings, he maintained it was
legitimate. He asked Monteiro to give Besa Mafia the benefit of the
doubt. “We are open to suggestions, we will do our best to make it the
best marketplace focusing on body harm revenge and property
destruction,” Yura wrote.
As evidence, Yura offered
to have someone of Monteiro’s choice beaten up. He then proposed to pay a
$50 monthly retainer to feature Besa Mafia banners on Monteiro’s blog.
When Monteiro declined both offers, Yura’s tone became menacing. “Be
neutral to our website,” he wrote. “Unless you do that, we will pay some
cheap freelancers to fill articles and submit posts and comments
claiming you are undercover cop.”
Monteiro published the exchange in full on his blog, mocking Yura and Besa Mafia. Weeks later, someone left a comment: a link to a video.
It started by showing an A4 sheet. ““[G]ang members for besa mafia on
deep web,” the sheet read. “[D]edication to pirate london, 10 April
2016.” There followed some 30 seconds of darkness, rustling and metallic
sounds. Finally, the camera turned towards a white car, engulfed in
orange flames. The sheet was shown again, metres away from the blazing
car. The video appeared to be a threat to whoever was running
pirate.london.
Monteiro was horrified: he thought
this was not the behaviour of a scammer. Online con artists ignore
people who call them out, he thought; they don’t set cars on fire to
defend their reputation. “I started questioning myself: had I pissed off
a criminal organisation?” he says. “What the fuck had I got myself
into?”
Monteiro works out of his living room in London
The
video prompted Monteiro to contact law enforcement. At London’s Charing
Cross Police Station, he told the officer behind the desk that he was a
cybercrime researcher – specialising in drugs, fraud and murder – and he
wanted to report a darknet assassin threatening him with videos of
flaming cars. “I just wanted to get this on the record,” Monteiro
recalls.
The officer was perplexed. Weeks later, the
case was passed on to the Metropolitan Police’s cybersecurity unit,
Falcon Team. Monteiro maintains that nothing came out of it: he says
that the officer said that the car did not seem to have been destroyed
in the UK and was therefore out of the Met’s jurisdiction.
Monteiro
also attempted to contact the UK National Crime Agency (NCA) – but, he
would later realise, he mistyped the email address and the message was
not delivered. (The NCA doesn’t send bounce-back notifications.)
Monteiro
resolved to explore the Besa Mafia website himself. He created a
customer account, calling himself Boaty McBoatFace and requested a hit
on a fictional person he called Bob the Builder. In doing so, he spotted
a way to gather intelligence on the website: each message sent on the
platform was assigned a unique numeric ID. By combining message IDs with
the website’s url, Monteiro discovered that he could read every other
user’s messages. Exploiting this vulnerability, he downloaded Besa
Mafia’s entire message database and examined its archive.
Sure enough, Besa Mafia was a scam. Every
conversation followed an identical template. Customers submitted the
details of the person they wanted killed and the method they preferred –
for instance, a hit that looked like an accident would be more
expensive. To prove they had the wherewithal to pay, they were required
to make an advance bitcoin transfer to a digital wallet – from which,
the website assured, its clients would be able to withdraw their funds
any time.
Yura would claim to take swift action,
before a period of prevarication: the hitman had been stopped for a
traffic violation, or for illegal possession of a gun. A more
professional assassin could be hired, but that would cost more bitcoin.
Some customers kept paying, as Yura led them on for months. Others
requested a refund, which never came. Yura kept all the bitcoin.
But Besa Mafia was more than just any run-of-the-mill scam: Monteiro realised that it was a fully fledged fake news operation.
Yura
devoted a lot of energy to defending the website’s credibility. A
California-based person going by name Thcjohn2 had written to the
website offering his services as an assassin. “[I] am broke (of course),
and am looking for quick cash,” Thcjohn2 wrote. “I have military
training (US Navy).” Instead of taking him up on his offer, Yura had
asked Thcjohn2 to make videos of burning cars to intimidate Monteiro and
other critics. He then asked him to enact and video a fake murder, with
the help of a friend and a replica gun. In the following months,
several videos of balaclava-clad thugs firing guns and talking up Yura’s
assassination websites would pop up online.
Yura had
also set up a galaxy of micro-websites on the regular web, which spread
the word about Besa Mafia under the pretence of denunciating it. Yura
had hired freelance SEO experts, who had optimised the sites to ensure
that they appeared first in search results for “hitman for hire” and
similar word combinations. One such freelancer, a Kolkata-based
consultant called Santosh Sharma, told me in July 2018 that Yura – who
had used the name of Andreeab when dealing with him – had paid him in
bitcoin. “He was based in Romania,” he said. Sharma says that he is no
longer working for Yura.
The marketing strategy seemed to have paid off.
After working his way through Besa Mafia’s messages, Monteiro had proof
he was right about the site being a scam – but that was little
consolation. “It was a fully functioning operation,” he says. “People
had been buying it.”
And there was a flipside to the
scam: the message archive was essentially a kill list – of targets, of
conflicts, and instigators. Of people who other people wanted to kill.
Yura had no hitmen to deploy, Monteiro thought, but what if some of the
website’s customers decided to take matters into their own hands, and
kill their target themselves? Could this archive be evidence – or even
be used to pre-empt murders?
“Most scams aren't
dangerous or don't feature dangerous people,” Monteiro says. “If you get
ripped off by a ‘Nigerian prince’, you're not dangerous – just stupid.
This scam was different, fundamentally different, from any scam I had
seen before. The people who are using it are the dangerous people, more
than the scammer himself. The clients are the bad guys.”
The
website attracted customers from every corner of the world. There were
some trolls who put in joke requests, but most users were serious.
Someone wanted his wife’s lover killed, his organs sold to get a
discount on the hit, and the woman herself smuggled into Saudi Arabia; a
Dutch user paid 20 bitcoin to have someone flattened in a fake cycling
accident; a person in Minnesota had spent four months chatting with Yura
about how to get a mother-of-one murdered.
Monteiro
turned for help to a friend of his – a scammer-baiter who adopted the
nom de guerre Judge Judy – and together they created a program to
systematically scrape messages from Besa Mafia. Judge Judy was solely
interested in disrupting Yura’s business. Monteiro, instead, started
compiling a list of the most dangerous users, ranked by how much they
paid and how determined to see the murder through they appeared.
Sometimes, he used information in the correspondence to find out the
website users’ identities; but he decided against getting in touch with
the targets mentioned in the messages, or leaking the archive online. “I
was hoping to work with the police, and what I didn't want to be was a
hacker who destroys evidence,” he says. “What if [the users] realised
they were exposed, and had hidden?”
He says he tried to get the police involved –
again, with little success. He claims that the Met referred him to the
NCA, which didn’t answer his calls or messages; the National Counter
Terrorism Security Office said that the matter was out of its
jurisdiction; the FBI suggested that he talk with the NCA.

Besa Mafia's website as it appeared after "Operation Vegetable"
On
July 3, 2016, Monteiro and Judge Judy launched “Operation Vegetable”. It
was the third hack Besa Mafia had suffered in four months. It would
also be the final – and decisive – one.
In late April
2016, a hacker known as bRspd had infected the website by uploading a
malicious file instead of the picture of a target. In that way, the
hacker seized the website’s message archive, its user IDs, passwords,
server passwords and admin emails; then dumped the whole lot on the
internet. The hack – together with a second, nearly identical attack
bRspd carried out in June – set several events in motion.
Yura
reassured his customers that the leak was not a big deal. “We are not a
scam. There are no bitcoin lost. Our website got hacked, but hackers
only got information about some users,” Yura wrote in a message to a
customer. “[T]hey did not stoled any bitcoin.” Meanwhile, he set about
launching a new, rebranded website.
Some media outlets covered the leak and Monteiro gave interviews on the matter – something that, in hindsight, put his name on Yura’s radar.
Together
with Judge Judy, Monteiro planned to build on bRspd’s work to bring
Yura down for good. Using information from bRspd’s dump, the two managed
to hack into the website; Monteiro even obtained access to Yura’s
Gmail. There, he snooped through the admin’s correspondence. He found
emails in which Yura talked about buying a much-needed English course,
messages to freelancers about advertising and shill sites, and data on
bitcoin payments. Combining this information with the content of the two
bRspd leaks, the duo obtained the cryptographic keys controlling access
to Besa Mafia’s website domain. “Me and my mate said, ‘Well, we appear
to have access,’” Monteiro explains. “Let's take the website down.”
There
was no long-term plan or complex rationale behind the decision. “I just
wanted to disrupt the operation,” Monteiro says. “It was also a
personal revenge. I can talk about the greater good... but it's
personal. It's many things – my individual focus shifts day to day.”
Monteiro
describes “Operation Vegetable”, as a carefully planned “Ocean's
Eleven-style” mission. They copied all of Besa Mafia’s content – and
saved it, Monteiro says, with a view to giving it to the police – and
shut the website down, redirecting users to a site they had built. The
new page showed the picture of a closed, rusty door. Under the Besa Mafia logo, they left a message:
“Besa Mafia has closed for business
After 6 months of scamming criminals for their bitcoins and stealing over 100 BTC ($65.000) the site has closed
No one was ever beaten up or killed ”
In the background, the website played that tune from The Sound of Music, “So long, farewell, auf Wiedersehen, goodbye.”
At Monteiro’s place, he and Judge Judy uncorked a bottle of champagne.

Long Reads
Evidence
of the first murder linked to Besa Mafia emerged shortly after Monteiro
met up with two police officers and seven months after Besa Mafia’s
takedown.
In January 2017, Monteiro managed to
establish contact with the NCA through a friend who knew someone in the
organisation’s intelligence unit. After some email exchanges with an
operative – who did not use his real name – Monteiro was invited for a
confidential meeting in central London.
For more than
an hour, Monteiro told the officers about the material he had come
across after penetrating the website’s messaging system – wannabe organ
harvesters, mutilation requests, people aspiring to commit matricide. He
suggested that the targets should be told what was going on and flagged
up that Yura, undeterred by the Besa fiasco, was now operating a new
assassination market, called Crime Bay. It used the same source code as
Besa Mafia, which conveniently allowed Monteiro to continue to read the
site’s correspondence.
Monteiro claims that the
officers said they would be in touch again for an information handover,
but did not ask him to show them the data he had brought to the meeting,
which was on his laptop. The only document they consulted was an A3
printout on which Monteiro had summarised the intricacies of Besa
Mafia’s operation.
Part timeline, part list, part
flow chart, the document included a breakdown of the various hacks and
dumps the website had suffered, and even a top 10 of the website’s most
dangerous users – in a fully wikified format. Always the wikipedian,
Monteiro had begun to structure his trove of Besa Mafia-related
information in a password-protected BesaWiki. One of the “most wanted”
users on Monteiro’s A3 was someone who went by the name of Dogdaygod.
Dogdaygod first messaged Yura in February 2016.
He was eager to kill a woman living in Cottage Grove, Minnesota. He was
open-minded about the method – initially pushing for a hit-and-run, or a
deliberate traffic collision, but later suggesting rasher systems, such
as shooting the target and burning her house down.
Dogdaygod
displayed a virulent animosity towards his target. “I need this bitch
dead, so please help me,” he wrote. Yura had egged him on: “Yes she is
really a bitch and she deserve to die.” The conversation went on for
months, coming to an abrupt conclusion when Dogdaygod – tired of Yura’s
increasingly implausible pretexts for why the hit had not been carried
out – requested a refund.
“Unfortunately, this site
has been hacked,” the admin had responded. He pretended to be the
hacker, hoping to stop Dogdaygod from badgering him, and make some money
on the side. “We got all customer and target information and we will
send it to law enforcement unless you send 10 bitcoin,” he wrote. That
happened on May 20, 2016.
On May 31, 2016, about a
month after the bRspd leak, the FBI contacted Amy Allwine, a woman
living at the Minnesota address Dogdaygod had submitted to Besa Mafia.
Amy and her husband Stephen Allwine – an IT specialist and a deacon at a
local church – met with officers who informed them that someone had
paid at least $6,000 on the dark web to murder Amy. The Allwines said
they had no idea of who could be hiding behind the Dogdaygod persona.
Six
months later, Amy Allwine was dead. On November 13, her husband called
911 and said he had found her body in her bedroom. “I think my wife shot
herself,” he told the operator.
However, the police
found evidence that linked Stephen Allwine to the murder: traces of
bitcoin transactions on his devices, cookies for dark web-related
websites, the fact that Dogdaygod had tried to buy the anaesthetic
scopolamine on the darknet – and that high doses of the substance had
been found in Amy’s system.
In
January 2017 Allwine – aka Dogdaygod – was charged with his wife’s
murder. In court, prosecutors pointed to a series of affairs – and the
fact that Stephen was the only beneficiary of Amy’s $700,000 life insurance policy – as probable motives. Allwine
was found guilty and sentenced to life in prison in February 2018.
Monteiro
says that he was devastated when Allwine was arrested. Up to that
point, the idea that he could have saved lives – that the kill list he
had been frantically trying to hand to law enforcement had a portentous
power – had essentially been a thought experiment.
“I
had been thinking: ‘Well, these are horrible, terrible people, who, if
you don't arrest them, maybe will take the matters into their own
hands,’” he says. “I thought that was hypothetical. But then it really
happened.” He texted his NCA contact about the development; the officer
reassured him that they would look into the matter urgently.
Weeks
went by. One Friday night in early February, Monteiro was at home
sipping pumpkin soup in front of his computer’s six glowing screens. His
desk was strewn with tokens of geekery: a self-destruction-style red
button; a stuffed Bulbasaur; a parody “Maybot user’s guide”. Monteiro
walked across his beige-carpeted living room, towards the front door: he
had heard a strange noise. Seconds later, a red battering ram smashed
through the white door and armed police officers rushed in. They pushed
Monteiro against the wall and handcuffed him. Seizing his computer, they
took pictures of the room and asked him for his devices’ passwords.
After about 15 minutes, they put Monteiro into the back of a van and
drove him to the nearest police station.
At the station, an NCA officer told him he had been arrested for incitement to murder, in connection with Besa Mafia.
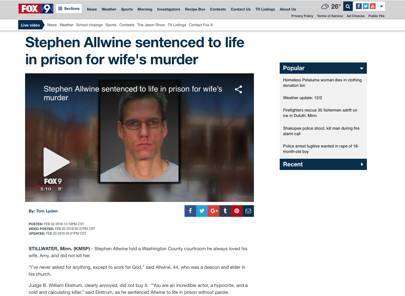
In
early 2018 Stephen Allwine, who had tried to hire a killer under the
false name "Dogdaygod", was sentenced to life for murdering his wife
It appeared that Monteiro had been arrested on the basis of a misinformation campaign.
There
had been warning signs for a while, at least since the point at which
Yura had threatened to expose him as a cop. In June 2016, when Monteiro
hacked into Yura’s Gmail account, he had noticed that the scammer had
created email addresses under the name of Chris Monteiro and Eileen
Ormsby, an Australian journalist who had also written about Besa Mafia.
Over
the following months, Yura had instructed his detail of freelancers to
create websites peddling fake news about Ormsby’s and Monteiro’s
involvement in the assassination marketplace. They were WordPress blogs,
not excessively sophisticated, but strong on SEO. Some had seemingly
caught the NCA’s eye: the application for the warrant to search
Monteiro’s flat referenced one of these blogs as evidence.
“Open
source reporting shows that Chris MONTEIRO and two other subjects
created the Hit Man for Hire website ‘Besa Mafia’ on the Dark Web https://hackeddatabaseofbesamafia.wordpress.com/,” the document read.
It
was imperative to search Monteiro’s place, the application for the
warrant continued, because, as the presumed site’s admin, he might be in
possession of more victim data and criminal evidence.
Monteiro
spent almost two days in a custody suite, working himself up, pacing
the cell and paging through the only book he could get his hands on – a
golfer’s autobiography.
Over the course of several
interviews with the officers who had arrested him, Monteiro understood
that the NCA agents he had spoken with some weeks earlier had not told
their colleagues that he was collaborating with them – and that, far
from being Yura’s accomplice, he claimed to be his self-appointed
nemesis. Monteiro says that, as he didn’t know his NCA contact’s full
name and he didn’t have access to his devices while in custody, he could
not immediately prove his dealings with the agency.
For
Monteiro, the interrogations were a mix of blundering and black comedy.
He had to explain the story of Boaty McBoatFace’s taking a hit on Bob
the Builder. At some point, the person questioning him asked Monteiro
about a copy of stealth videogame Hitman found in his flat, implying
that it could have been an inspiration for Besa Mafia.
Eventually,
Monteiro succeeded in explaining to the agents that they should look at
the BesaWiki on his computer. There, they would find everything they
needed: target names, messages, data on bitcoin payments, server IPs and
information on how to backdoor the Crime Bay website. At midnight, on
Sunday February 5, Monteiro was released on bail.
He
went back to his flat and guessed he’d have to change the door’s frame.
Monteiro stayed at Judge Judy’s place that night. They played N.W.A’s
song “Fuck tha Police”.
In June 2017, the police informed Monteiro’s lawyer that no further action would be taken.

Long Reads
Shortly
after, the NCA launched an international operation. They tracked down
several Besa Mafia users and charged them with conspiracy to commit a
crime.
In March 2017, they arrested David Crichton, a British doctor who had ordered a hit on his former
financial advisor. Crichton did not pay the website, though, and later
said he had put in the order just out of frustration; Crichton was
cleared of any wrongdoing in July 2018. Another Crime Bay user in
Denmark, an Italian-born woman called Emanuela Consortini, was arrested thanks to an NCA tip-off and then sentenced to six years in jail for
commissioning the murder of an ex-boyfriend. The Crime Bay website was
eventually shut down by the NCA and the Bulgarian police in May 2017 and
Monteiro assumed that Yura had been found and jailed. Monteiro stopped
researching the matter.
Then, in December 2017, he
received an email from Yura. The scammer accused Monteiro of being
immoral: his exposing of Besa Mafia as a scam could have caused users to
stop wasting time and resources on the website and kill their targets
themselves. He called Monteiro Amy Allwine’s real killer. “How is Yura
sending me emails?,” Monteiro thought. “How is he not in jail?”
The
full extent of the situation emerged in early 2018 when CBS’s 48 Hours
approached Monteiro regarding the Allwine case. They wanted to interview
him about his run-in with Yura.
While preparing for
the interview, Monteiro discovered that Yura had launched a new website,
Cosa Nostra, and adopted a new persona – Italian capo “Barbosa”.
Monteiro’s exploit still worked and he could read all the messages
between Yura/Barbosa and his customers, just as he did back in 2016.
For
some time, Monteiro entertained the hypothesis that the new website may
be a police decoy. But it seemed unlikely: when Monteiro started
providing CBS with details about conversations from Cosa Nostra, it
would always be CBS’s subsequent tip to the local police force that
triggered investigations and arrests. “I started realising that people
were getting arrested directly as a result of the information I
supplied,” he says. CBS’s tips led to arrests in Singapore,
Illinois and Texas. When Monteiro passed me some documents about
customers in the UK, I forwarded the details to police stations in
Edinburgh and Oxfordshire.
Monteiro tried again to
pass the matter to the police. He had his lawyer email the NCA, telling
them about murderous plots hatched on Yura’s website, which was
continuously rebranded – Cosa Nostra, Sicilian Hitmen, Camorra Hitmen,
Ndrangheta Hitmen, Yakuza Mafia, Bratva Mafia. Through his lawyer, the
NCA advised Monteiro to call their hotline to report possible offences;
they warned him about using illicit means to access the assassination
markets’ correspondence.
“The threat posed by
so-called assassination markets is going to be pretty small in
comparison to other things we deal with,” an NCA spokesperson told me.
“We aren’t monitoring the website [and] there have been no arrests.
However, we work closely with our international law enforcement partners
to share information and intelligence,” a second spokesperson later
added.
That leaves Monteiro stuck with the list and
an apparent strong urge to act, by sending the most plausible cases to
the media. “I want to create a bit of a splash about this thing,”
Monteiro says. “Selfishly, I want to give talks [about assassination
markets], and use it as a platform to put further pressure on the
police.” But he also feels that he has a duty to try and act on the
information he retrieves. “I can't stop because there are people's lives
at risk. Imagine you'd looked into a box and the act of looking into
that box changed you. You can choose not to look into that box. But you
knew that something would still be going on: the box is full of horrors.
Should you look? Should you not look?”
Monteiro
keeps looking. He set up Google alerts for every target’s name – in case
something happens to them, even if the authorities have been alerted.
That’s how he spotted the news about Bryan Njoroge in a local Indiana
outlet, the News and Tribune.
According
to Clarksville PD’s case reports, on June 8, Njoroge, a 21-year-old
Texan on leave from the Fort Knox base, stole a gun from a shooting
range, American Shooters, in the town’s north-west. Njoroge was found
dead in the early hours of June 9, face down under the stairs of an
announcer’s box on a baseball field. The coroner quickly established
that he had died of a self-inflicted gunshot wound. The case was closed
within days.
Whoever ordered the hit on Yura’s scam
website knew that Bryan would be in Indiana on those days; more
specifically, they knew he would stay at a specific Airbnb, the address
of which was included in the order instructions. Njoroge’s father,
Samwel, confirmed to me that his son had booked that Airbnb.
“We’re
done with the case,” the officer in charge of the investigation at
Clarksville PD, detective Ray Hall, told me in August. He said that he
had already received a tip about the Toonbib conversation and that
nevertheless had found “no factual evidence” of anything other than a
suicide taking place.
Samwel Njoroge told me that the
police had never mentioned the assassination market when talking with
him about the case. He was not happy with how his son death’s had been
investigated, pointing to what he thought were inconsistencies between
the case report detailing the discovery of the body and the autopsy, and
underlining that the fatal bullet has never been found. (A forensic
pathologist told me that bullets often go unretrieved in suicide cases.)
Samwel
added that Bryan’s computer, camera and two phones had vanished, which
is strange, as Bryan – a small-time Instagram and YouTube celebrity –
was inseparable from his devices. He also mentioned that his son had a
$400,000 life insurance policy; Njoroge had changed the beneficiary –
designating a female friend instead of his parents – just a month before
dying.
Samwel said he did not know whether someone else could have been travelling with Bryan, or known about his trip to Indiana.
Bratva Mafia is the latest iteration of the Besa Mafia killer-for-hire scam
We
know little about Yura: he (everyone I spoke to who had interacted with
Yura believed him to be a man) boasts to have made a lot of money –
which is possible, especially in light of last year’s spike in bitcoin
price; he claims to be Albanian, but Santosh Sharma’s recollection and
Monteiro's IP analysis of Yura’s comments on wikis link him to Romania;
Eileen Ormsby, who has had multiple email conversations with him,
believes that Yura is likely to be in his twenties.
Maybe
the most interesting question, though, is whether Yura, aka Barbosa, is
a police informer. He certainly tries to style himself as one of the
good guys. When we exchanged emails he implored me not to say that his
website was a scam.
“If you intend to report hitmen
scams, you are basically siding up with those would be murderers,
helping them to avoid scams and traps and helping them to find other
means to do their kill,” Yura/Barbosa wrote. “[It] is a moral right to
scam criminals and would be murderers if this helps saving victims.”
He signed off his messages “Barbosa, Lifesaver”.
His
defence is that he is a hindrance to potential murderers’ plans,
robbing them of precious time and money. More significantly, he said
that he was giving all target information to the police, and maintained
that he has been working with the FBI.
“After Besa
Mafia was hacked, FBI agent talked with me on chat on site. He told me
they don't want to arrest me, they are not after me, they want to arrest
the murderers,” Yura/Barbosa, wrote. “They don't care about a scammer.
They care about murderers.”
Yura refused to provide
evidence of his communications with the FBI, as that would prove that
his website is a scam. Pleading with me not to report that, he offered
to hand over the names of all the targets. He finally said he would deny
ever speaking to me if I wrote that his business was a scam.
What
Yura said was a blend of facts, factoids and lies. It is true that Yura
has passed information to journalists who approach him in order to
establish his credentials as a good-hearted scammer: he handed two cases
to CBS, which then turned them over to the police, triggering
investigations and arrests.
And some conversations
in the bRspd dump do show that Yura had contacts with someone claiming
to work for the FBI’s Dallas office as early as 2016. The FBI declined
to confirm or deny whether it had ever worked with Yura.
Other
things Yura says are untrue. He maintains to have never condoned
violence, but there is evidence of his trying to pressgang Thcjohn2, the
wannabe hitman, into committing an assault – which apparently never
materialised.
His overall narrative of being a
killer-baiter in shining armour doesn’t hold water. bRspd, the hacker
who in 2016 twice broke into Besa Mafia’s website, told me over private
chat that he had approached Yura about turning Besa Mafia into an actual
honeypot for criminals. “I was trying to work with him by making the
website better and more secured [sic] and instead of scamming we could
really help people to identify these criminals and etc by collecting
more data & NOT stealing people money,” bRspd wrote in September.
According
to bRspd, Yura refused. “He was just thirsty for money,” bRspd told me.
“He's a big liar, he doesn't care about anything but money. Almost all
the conversations I had with him included the word ‘money’ or
[bitcoin].” According to Monteiro’s analysis of Besa Mafia’s bitcoin
wallets, Yura might have amassed nearly £5m.
bRspd added that the notion that Yura was working with the police was – at least as of 2016 – “totally false”.
In
general, though, does Yura have a point? Without his scamming, some
lives would have been at risk and some people plotting murders would
still be around. Without Yura, neither Monteiro nor law enforcement nor
journalists would have ever heard of Stephen “Dogdaydog” Allwine in
Minnesota, the man in Singapore, or the woman in Denmark. Yura’s greed,
tenacity and SEO strategy had unwittingly created a tool to perceive the
intentions of would-be criminals.
I posited the question to Monteiro over a beer in a London pub. Was Yura providing a service to the community?
The
matter, Monteiro argued, boiled down to a philosophical debate between
virtue and consequentialism. Yura could make the case that his website
was being used to jail criminals. But he was doing that by inciting
murder, by egging criminals on and by spreading lies – about hitmen,
about other people and about the dark web.
The whole
Besa Mafia sorry saga, Monteiro says, started because he wanted to
cleanse the public sphere of lies. “I set out to bump off fake news. I
wanted to explain the dark web, establish facts and fiction, explain
what's real and what's not,” he says. “That’s my higher purpose – you
know?”
Updated 05.12.2018, 10.13
GMT: This article has been amended to correct a date in the Toonbib
correspondence: Barbosa replied on June 1, not June 6.